Cybersecurity Career Paths: Threat Intelligence & Threat Hunting
Threat Intelligence & Threat Hunting
Previously we talked about Detection & Response and what the job entails. In this issue of the series, we’ll dive into 2 more roles within the Blue Team in Cybersecurity:
Threat Intelligence & Threat Hunting. These are generally closely aligned.
Let’s take a look at these two domains within Cybersecurity.
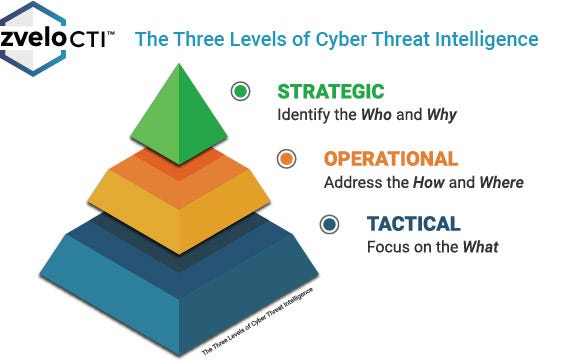
Threat Intel
Threat Intelligence professionals collect and analyze information about potential threats to the company. They use this information to help identify and mitigate risks and develop strategies for responding to attacks, usually in collaboration with partner Security teams. In the end, the work will be tailored to their organization.
A day in the life of a Threat Intelligence Analyst could include tasks such as:
Sorting and filtering data on potential threats.
Investigating threats to track their sources and develop preventive action plans.
Collaborating threat hunting efforts by creating hypotheses about potential attacks.
Prioritizing cyber defenses based on the scale and risk of threats.
Generating intelligence reports for other stakeholders.
Performing regular threat research to better understand the context of threats
This is not an exhaustive list, but a good overview of what to expect in the role.
Let’s dive deeper into this sample job description.
Sorting and Filtering Data on Potential Threats: A Threat Intelligence Analyst works with vast amounts of data. This data, sourced from internal networks, external links, and technical sources, needs to be organized, sorted, and filtered for potential threats. The process involves removing the noise and focusing on the signal—identifying potential threats and eliminating irrelevant data. This critical step allows analysts to focus their efforts on the most pressing threats.
Investigating Threats to Track Their Sources: Once potential threats are identified, the Threat Intel Analyst investigates to determine the source and the nature of the threat. This involves understanding how the threat started, where it came from, and what potential damage it could cause. By developing an understanding of the threat's origins and impact, the analyst can create an action plan to shield the organization from similar threats in the future.
Collaborating on Threat Hunting Efforts: Threat Intel Analysts play a key role in threat hunting activities (If a company is fortunate enough to have both a Threat Intel and Threat Hunting team). They create hypotheses based on the data collected and the intelligence gathered. This involves asking questions like, when did the attack occur? What was the attacker looking for? What systems were targeted? The hypotheses help in understanding how the attacker thinks and where to look for more threat intelligence.
Prioritizing Cyber Defenses Based on the Risk of Threats: Not all cyber threats are created equal. Threat Intel Analysts understand the impact of various political and current affairs on an organization’s security risks (if applicable). They also have complete knowledge of several threat types, including Advanced Persistent Threats (APTs), and their infrastructure. This understanding enables them to prioritize cyber defenses and define an action plan against specific attacks based on the scale and risk they pose to the organization.
Generating Intel Reports for Other Stakeholders: Communication is a crucial part of the role. After identifying, investigating, and prioritizing threats, they generate intelligence reports to share with the organization’s security operations staff, management, and other stakeholders. These reports provide an overview of the current threat landscape, the actions taken to mitigate identified threats, and recommendations for future actions. This keeps everyone in the organization informed and aids in making informed Cybersecurity decisions.
Performing Threat Research to Understand the Context of Threats: Threat Intel Analysts continuously perform threat research to deepen their understanding of the threat landscape. This involves technical research, intelligence research, and communication of these research findings. This regular research helps to unravel additional context and scale of threats, leading to a better understanding of what is known about a threat, why it matters, and what's unique about it. A key piece here is knowing the likelihood of a threat and its impact to the company.
It's an essential part of staying ahead of the rapidly evolving Cybersecurity landscape.
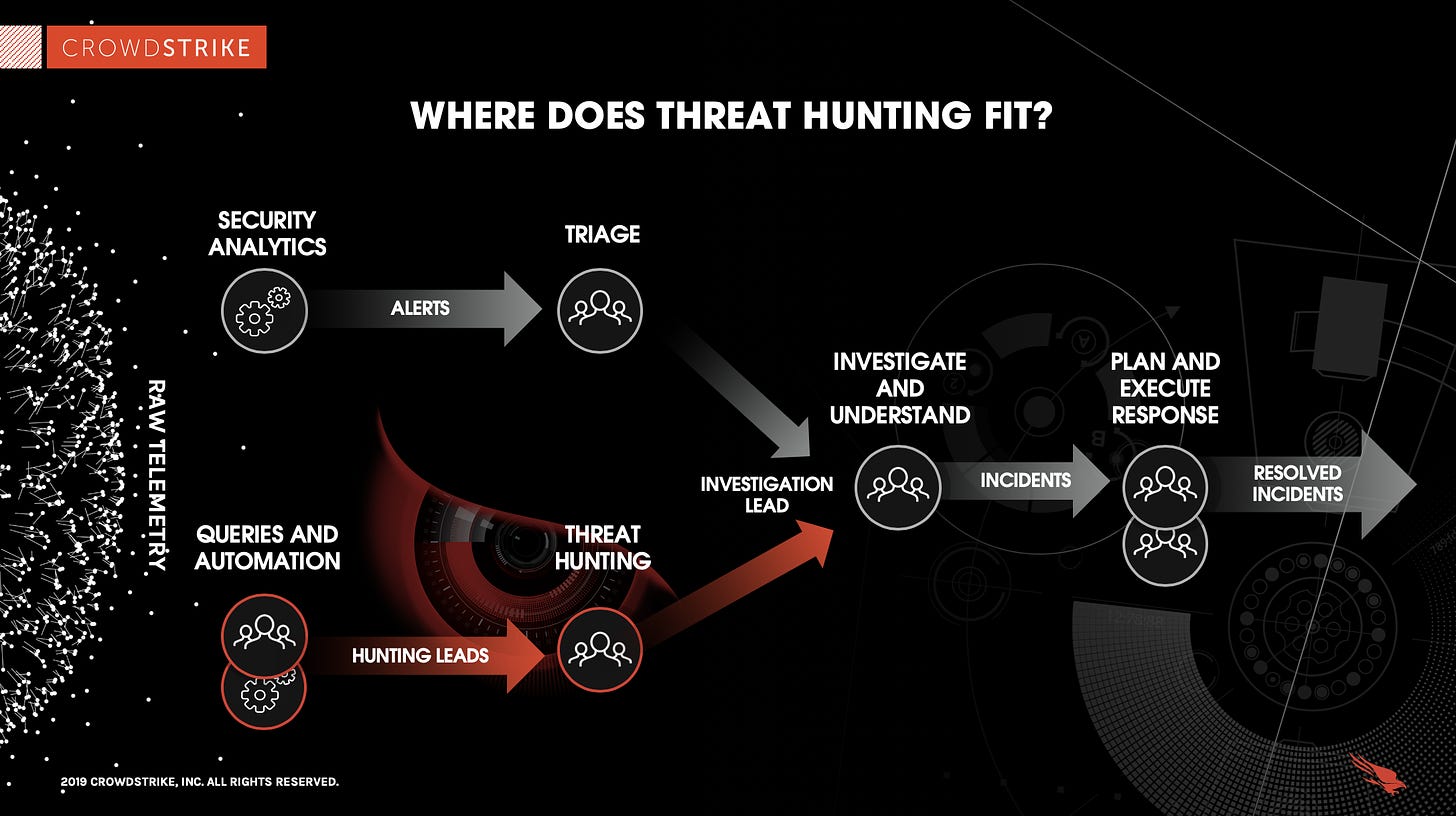
Threat Hunting
Threat Hunters proactively search for potential threats, focusing on areas not currently covered by automated detection systems. They use a variety of tools and techniques to identify suspicious activity, then work diligently to investigate and respond to these threats.
A day in the life of a Threat Hunter could include tasks such as:
Threat Hunting Research & Planning
Data Analysis
Investigation
Collaboration with the Blue Team
Documentation and Reporting
Let’s dive deeper into this sample job description.
Threat Hunting Research & Planning: Start the day by reviewing the current threat landscape, noting any emerging trends or unusual activity. Use this information to develop hypotheses about potential threats, which will guide the day's threat hunting activities. Also, research from the Threat Intel team could be surfaced to the Threat Hunting and they’ll use this as a lead.
Data Analysis: Once a hypothesis is formed, it's time to dive into the data. This involves analyzing logs, network traffic, and other data sources to identify anomalies or suspicious activity that could suggest a threat.
Investigation: When finding something that looks out of the ordinary, Threat Hunters will then start investigating. This could involve anything from timelining logs, deep-dive network forensics to malware analysis.
Collaboration with the Blue Team: If the investigation uncovers a credible threat, collaboration with the rest of the Cybersecurity team (the 'Blue Team') will ensue to develop and implement a response strategy. This might involve patching vulnerabilities, taking systems offline, or closing off ports.
Documentation and Reporting: At the end of the day, documenting your findings, making note of the threats identified, the steps taken to mitigate them, and recommendations for future action is key. This information is invaluable in strengthening the organization's security posture and preparing for future threats of similar nature.
Conclusion
Both Threat Intel and Threat Hunting are challenging but rewarding career paths. Offering an opportunity to be on the front lines, proactively identifying and combating threats.
If you're a problem solver with a keen interest in Cybersecurity, this could just be the career path for you.
Stay tuned for part 5 of this series, where we will dive into another aspect of Cybersecurity.