Cybersecurity Career Paths: Detection & Response and Incident Response
Detection & Response and Incident Response
I will be doing a deep dive on Detection & Response and Incident Response in this issue, this is part 3 of a 5 part Cybersecurity series.
This is the area within Cybersecurity I focus on myself today. With 6 years of experience in the Security Operations, Detection & Response and Incident Response area, I have gained insights into these domains.
The day to day can vary as our scope is wide but in a nutshell, it can consist of:
Ingesting logs as data sources
Writing rules to alert on various threat activity
Responding to an open port that needs to be shut down and root caused
Analyzing logs to tell a story of what events have taken place
Running projects that will enhance the maturity of the team
The goal is to minimize the threats the company faces and detect as early as possible.
Detection & Response can be done through endpoint (laptops), network, email, or cloud.
Some of the skills necessary for this field are, constant workflow streamlining, managing ambiguity, familiarity with attack frameworks, and Security Operations experience.
From here you can make a career out of specializing in SIEM (Security Information and Event Management). For example, Splunk, SumoLogic, ELK, etc. This means ingesting logs for the Security teams usage and then using them to detect threats and suspicious activity. Forming queries and detections to alert on said threats.
Detection Engineers build, test, and deploy systems that validate security controls and detect suspicious behaviors. The goal is to protect the “Crown Jewels” and prevent or detect incidents in the company.
Getting started as a Detection Engineer involves mapping and classifying systems (and data) by importance. Then, with this understanding, detections are created that flag varying degrees of behaviors by severity. For even more on Detection Engineering, see this previous post.
At the end of the day you can’t detect what you can’t see. So it all starts with the data.
Another area you can pivot to from Detection & Response (or vice versa) can be Incident Response (IR), which we’ll discuss next.
Incident Response
Incident response is sometimes used interchangeably with SOC as it is generally conducted by the same team. Although it can be a team on its own. In this area of Security, operating under pressure and being able to coordinate moving parts is crucial.
You can think of this area of Cybersecurity as paramedic work, often working in adverse circumstances but needing to execute the task at hand. When you read about a breach and all the work that was done in recovery of it, you can bet the Incident Response team was behind the scenes coordinating the efforts to remediate. This last piece of the job as Traffic Control, needing to be able to coordinate the moving parts and keep order in an otherwise stressful situation.
Some of the skills necessary for this field are: calm under pressure, effective writing skills, good cross-collaboration skills, and security tools knowledge. If you can effectively write up reports and post-mortem actions, directing traffic on what needs to be done in an incident, this is what is needed for this role.
Someone could make an entire career in Incident Response as it is always in demand and is a skill sought after.
As these domains are closely related, professionals often pivot between Detection & Response and Incident Response roles in their cybersecurity careers. You can move from Detection & Response, or from Incident Response to Detection & Response. A lot of the times in practice however, these can be the same team.
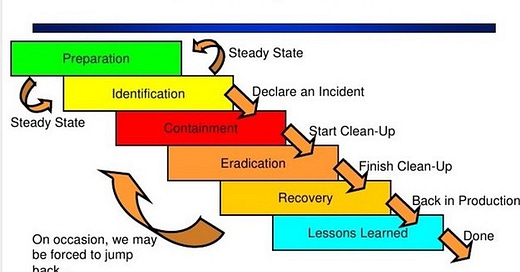
For more details on the Incident Handling lifecycle see
https://www.sans.org/media/score/504-incident-response-cycle.pdf
Conclusion
Hope this was helpful in understanding the career path and domains of Detection & Response & Incident Response.
As we’ve seen here, both Detection & Response and Incident Response play crucial roles in cybersecurity. They are both high in demand areas of Cybersecurity, and either of these paths will be very promising. They provide the critical defense mechanisms that organizations rely on to secure their 'Crown Jewels'.
While the roles vary, they share common ground in terms of goals: reducing risk, detecting threats, and responding to incidents effectively.
Stay tuned for part 4 of this series, where we will dive into another aspect of Cybersecurity.