Picking up off of last year’s recap of breaches. We’re going to go over breaches of the year and the patterns seen in them.
For the 2023 Recap of Company Breaches see this post
This year, there was a mix of HealthCare companies, technology companies, and data brokers, that were most impacted.
Note: I purposefully did not include the reports of Telco companies having persistent access from China-linked Salt Typhoon. This is still in flux, and I may write a full post on this.
A snapshot of the last 12 months
Health Care Records Anyone?
23andMe (Continuation of last year)
Now let’s get into more detail on the impact of these.
Deep Dive
If there were any themes in the data breaches of the year it was PII leaks to third-party vendors, and Credentials stuffing.
In many cases such as with AT&T or DHL, third-party was the point of entry.
This will continue as most companies work with a lot of vendors for their different business needs. The risk is therefore spread out and not on any one company.
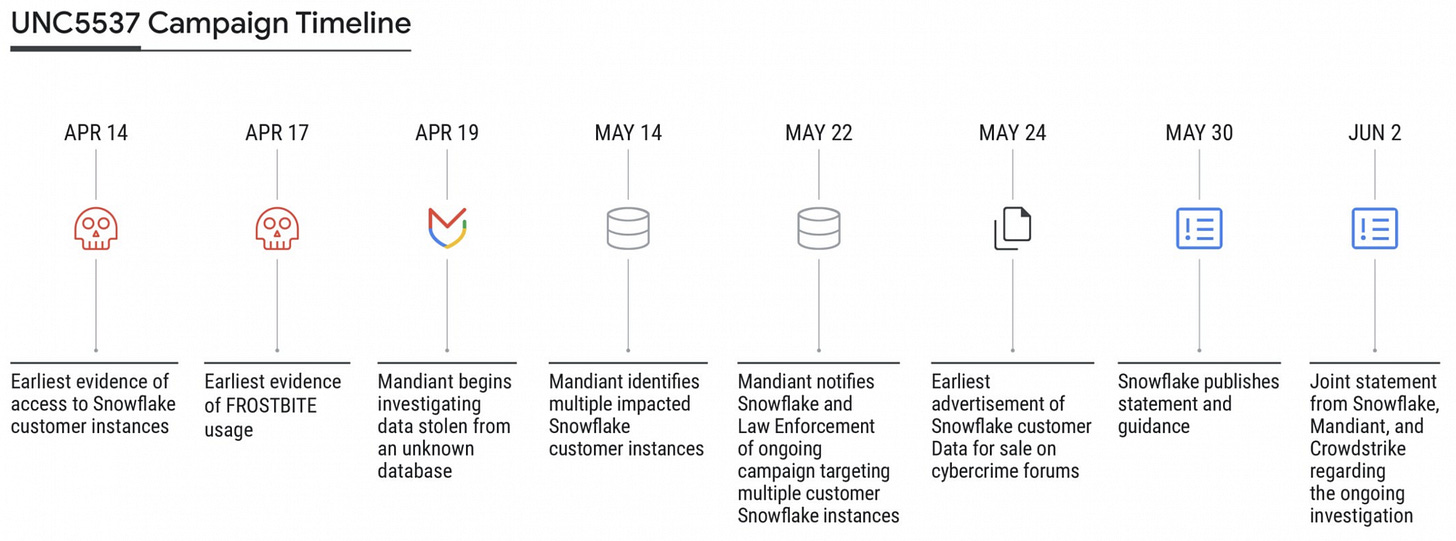
The AT&T breach was significant as it affected pretty much all of its customers. This stemmed from attacker access to the companies’ Snowflake accounts via credential stuffing and supply chain attack. This same third-party incident affected several other companies including TicketMaster, Pure Storage, and QuoteWizard/LendingTree.
A common denominator on the impacted was a lack of multi-factor authentication set up.
Then there’s OpenAI being fined on multiple occasions for data violations.
Seeing a theme here? Privacy is going to be a long battle.
Another theme that stood out was the sheer volume of records impacted.
AT&T mentioned above, had 109 Million customers impacted.
Now on the HealthCare front. Take ConnectOnCall for example, a breach that affected over 900,000 people’s records.
23andMe completed their investigation from the 2023 breach, totaling over 6.4 million affected. Totaling close to half of its customers. (Tried to warn friends about this one)
HealthCare companies have not figured it out yet.
Care1, ConnectOnCall, DeltaDental, HealthEquity, Kaiser, UnitedHealth, 23andMe have all been impacted in breaches or data leaks in the past 2 years.
Look, Security is hard and is something that is never truly done. However, these companies have historically been behind in their technology and Cybersecurity practices. This year was a snapshot of that mainly on the best practices front.
With data leaks, and breaches being rampant in this space, and credit monitoring services being the usual band-aid post-breach.
Of course, we can’t have a briefing on 2024 without mentioning CrowdStrike. This was not a Security breach, but a misconfiguration that resulted in an availability debacle. (That’s the “A” in the CIA triad)
The ramifications of this hadn’t been seen before at this scale as companies had entire systems offline for extended periods of time. Just ask Delta Airlines, with around 7,000 flights cancelled due to the software upgrade gone wrong. This was called the biggest outage in history.
A lot of times, it’s a not a breach but an availability outage that is the most impactful for a company.
What Can We Do About This?
Although company circumstances could vary in difficulty of implementing these, the following are preventative mechanisms to take inline with the breaches discussed today.
Prevent access to only managed devices
Multi-factor authentication all the things (seriously it’s 2025)
Utilize hardware security keys as a second factor, prevent all other forms (within reason)
Review Vendors and their Audits upon onboarding
Limit Cloud sharing access controls (Google Drive, Box, Dropbox, etc.)
On the personal security front, here are some steps we can take.
Multi-factor authentication
Utilize hardware security keys as second factor where possible
Review third-party apps & services in your (Google, O365 etc.)
And lastly, know your privacy rights. Acts such as CCPA, CPA, VCDPA, GDPR, etc are there to give the consumer a choice on their data. Most people just don’t know about them.
What I Read This week
How We are Self Hosting Code Scanning at Reddit: How the 4 person AppSec team supports ~2200 repos
Self-hosted scanning utilizing TruffleHog and OSV allowing code scanning at scale
A Primer on JA4+: Empowering Threat Analysts with Better Traffic Analysis
Building on the principles of JA3, with added capabilities.
Data Engineering For Cybersecurity Part 4: Data Transformation
Gave this a re-read. How data transformation usually goes, and how Monad can help here.
Wrapping Up
Going forward it looks like third party and supply chain will continue to be big areas to focus on as the attack surface continues to go from the company itself onto the companies it does business with.
There are only two types of companies: those that have been hacked and those that will be. - Robert Mueller
With the increased impact of breaches and data leaks, security is everyone’s responsibility, from the Security team, to the individual employee.
Hope you learned something new about this years breaches in this writeup.
See you in the next one.