Newsletter Issue #181: What I Read This Week
If you haven’t already, check out last week’s post about the future of SIEM. It’s a conversation being had in most companies now.
Will be writing a part II on this soon.
This week’s stories were a mix of developments to past weeks stories, legit DFIR tools being used again for malicious purposes and more Discord related news.
Now, let’s get into it.
What I Read This Week
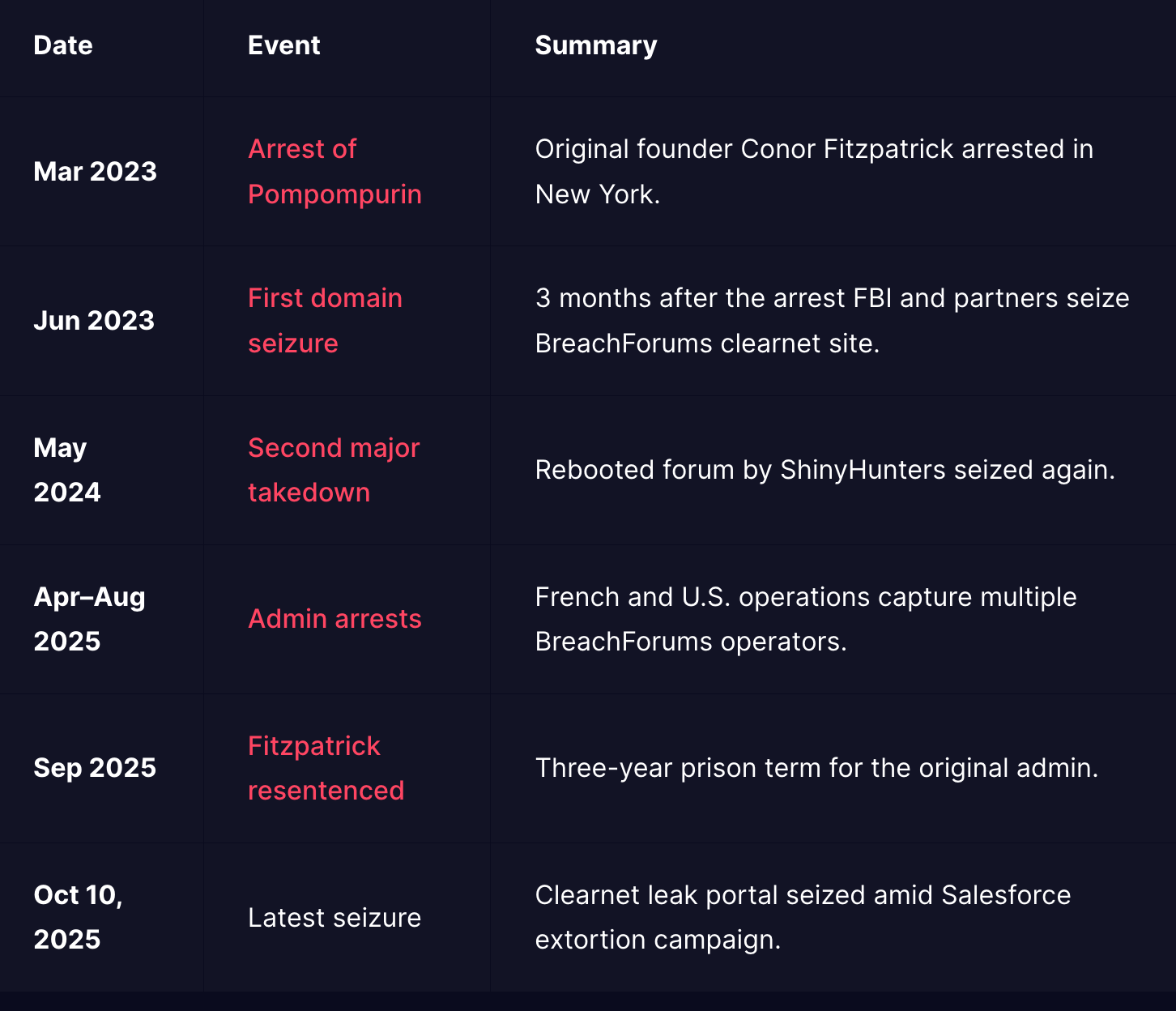
BreachForums Seized (Yes, Again)
This forum has taken down previously, but within days, the same domain resurfaced to publish data stolen from Salesforce customers
Another positive development in this saga
A timeline of BreachForums in context
What the 2025 Elastic Global Threat Report reveals about the evolving threat landscape
Elastic Security Labs goes over highlights for the telemetry they have seen over the year
Browser Creds are in: Their analysis of 150,000 malware sample showed more than 1 in 8 are designed to steal browser based credentials
Germany slams breaks on EU’s chat control
“Random chat monitoring must be taboo in a constitutional state” - Federal Justice Minister Hubig
The point of age verification has also come up (See last week’s Discord breach why this is a problem)
Interesting, one of a couple countries in the EU actively opposing the surveillance trend
How to tell if your phone number has been hacked (How to spot a SIM Swap hack)
“The best advice is to stop using SMS and start using stronger forms of authentication.” Couldn’t agree more
I’ve written in the past about this threat model and how to protect yourself
Weaponizing Discord for Command and Control Across npm, PyPI, and RubyGems.org
In recent months, malicious packages in npm and PyPI, have been making headlines siphoning telemetry from developer machines
The Socket.dev team identified this technique after network monitoring flagged an unusual spike in POST requests to discord[.]com/api/webhooks/
Velociraptor (version 0.73.4.0) leveraged in ransomware attacks
Attackers (Storm-2603) leveraged Velociraptor, the open-source tool, abusing it to deploy ransomware
They used an outdated version, vulnerable to privilege escalation via UpdateConfig artifact for stealthy persistent access
Why Signal’s post-quantum makeover is an amazing engineering achievement
Signal Messenger rolled out a major upgrade to its encryption protocol, gearing up for the Quantum Apocalypse
The phrase “use Signal” has been pretty much synonymous in the Security community
Wrapping Up
In this post, we covered some of the top stories from this week.
See you in the next one.