Newsletter Issue #179: Linux Toolbox
Tool Series
I have previously talked about domain areas that are fundamental when it comes to learning about Security.
Although there are several, (more that can be covered in one post) here are a few that stand out are the following.
Network Fundamentals
OS Fundamentals (Any OS)
Cloud
Learning Linux
These are areas that will pay dividends that you can’t really skip even with all the buzzwords going around.
A common denominator that touches all of these is Linux. I’ve talked about the power of Linux several times, and how versatile it can be.
For example, in the Tools series.
Linux is the most widely used open source operating system.
Within Cybersecurity, where the “function over form” principle takes precedence there are many ways it can be utilized for better working systems and more secure environments.
When using Linux for any use case in compute or security, it will usually be via the command line.
Thinking of operating out of the GUI as driving automatic, and working out of the command line as driving stick shift 🚗⚙️ (any car person can tell you the difference) can help model the benefits here.
I won’t spend too much time going over the many powerful use cases for Linux, as I have done so in previous posts.
Instead, let’s go over some resources that will aid in up-skilling or refreshing with Linux.
Resources
There are many out there, but here are some concrete resources that can aid in building Linux skills or getting in reps over time.
CommandLineKungFu
CyberDefenders
OverTheWire
explainshell
Free Course
CommandLineKungFu
A blog I have recommended to people wanting to get their hands dirty with the command line. It goes over specific problems and solving them from the command line. It focuses on the “how”, with walk throughs on solutions from experts in the field.
CyberDefenders
A hands on platform with Capture the Flags. It has various challenges in security topics and sets of questions to go through.
It is focused on the Blue team side of things, and can be good practice for hands on learning. They have a certification as well that could be worth checking out.
OverTheWire
A CTF style wargames platform. You can start from basically zero and it levels you up by the end, with challenges increasing in difficulty as you go. You can think of these as reps.
This option will be less structured and more free flowing than studying for a cert.
I recommend starting at Bandit, based all on the command line.
explainshell
A cool web based tool that parses man pages, and full command lines. It’ll provide help messages for each piece and argument of a command line.
We can finally know how tar commands work without googling (we’ve all been there).
My Course
Lastly, a while back I created a free course, an Intro to Linux.
It’s an introductory course into the command line, its fundamentals, and navigating man pages. It will always remain free for the community.
Linux Command Line Fundamentals - Free Course
If you’re going to be working with servers, chances are they will be running Linux.
If you are working in a Cloud environment, chances are this is going to be in Linux. In fact, approximately 90% of the public cloud workload operates on Linux.
What I Read This week
First off, the Sora 2 stuff is wild. I can see malicious parties utilizing this for attempts at incriminating public figures via AI generated content. (← this once is a joke obviously)
Time will tell if this will be a thing, but my money is on that it will be.
Okay, with that out of the way let’s get into it.
First Malicious MCP in the Wild
Koi discovered an MCP that was stealing user emails via a BCC line, this had 15 legitimate version before this malicious one
The malicious piece to the software? One line
Don’t Sweat the *Fix Techniques
One TTP walk-trough for ClickFix: Fake interstitials for interaction, clipboard copy, pull the payload
This post also goes over strategies to detect iterations it created in parallel
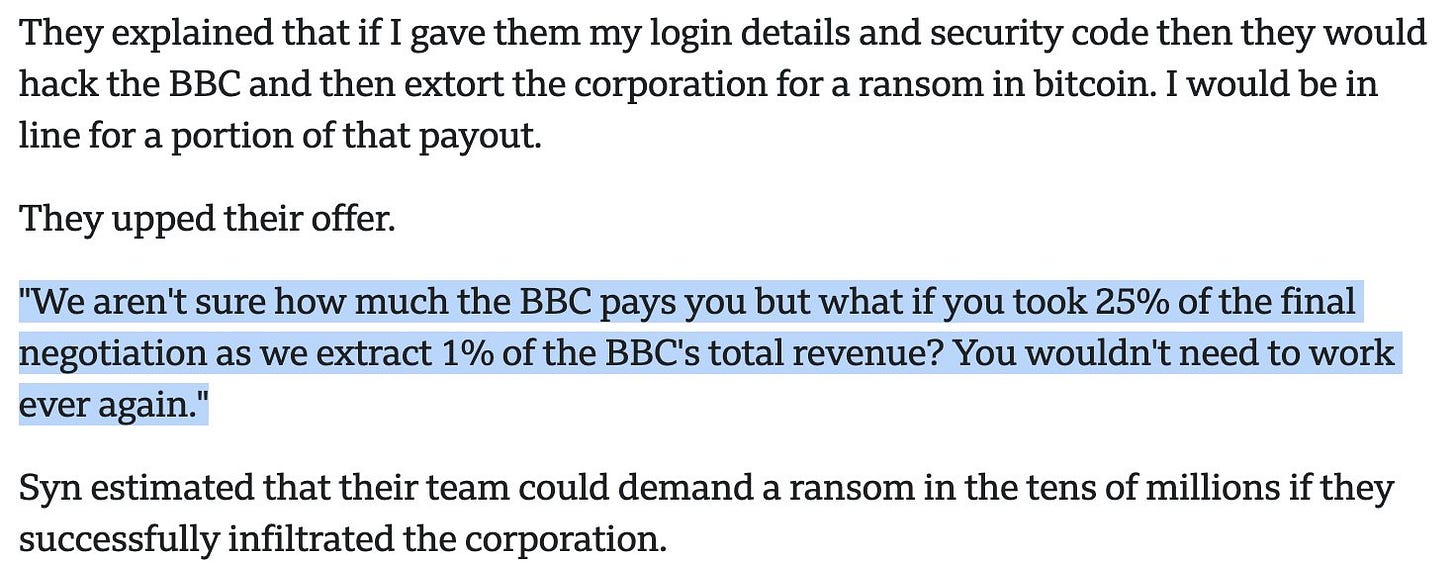
‘You’ll never need to work again’ Criminals offer reporter money to hack BBC
A closer look at how insider threat looks like, from the inside
They even offered a 0.5 BTC deposit as a “trust payment”
Our Plan For a More Secure NPM Supply Chain
Some plans include deprecating legacy tokens, TOTP, moving towards FIDO based 2FA, shorter lived tokens, trusted publishing
Always interesting to see how others deal with the same problems everyone faces, from the source
Will Security Companies Disappear?
After getting past the headline, this post comes down to the fundamental question companies are facing “Do we need this security tool?”
“Palo Alto’s acquisition of Protect AI, CrowdStrike’s purchase of Pangea, Check Point’s grab of Lakera, all of these show that legacy firms know they need this muscle.”
Lastly, wanted to point out the SANS Summit happening today and tomorrow (recordings will be available if you register)
Some of the talks include:
Snakes on a (Control) Plane
Ghost to Guardrails: Beyond the Alert Driven Posture
Wrapping Up
Linux is a difference maker in many ways in Cybersecurity.
I hope the community will continue to find value in the course and get the most out of it.
See you in the next one.