Newsletter Issue #176: What I Read This Week
A lot happened this week, some good and some bad. From updates to a story from previous posts, to supply chain attacks.
I kept it to the 7 stories that stood out the most to me.
Let’s get into it.
What I Read This Week
Addressing the unauthorized issuance of multiple TLS certificates for 1.1.1.1
This was issued by the CA, Fina (to themselves) without proper checks for the requestor having legitimate control over 1.1.1.1
“While we regret this situation, we believe it is a useful opportunity to walk through how trust works on the Internet between networks like ourselves, destinations like 1.1.1.1, CAs… and devices like the one you are using to read this”.
Hats off to Cloudflare for this response
How North Korean hackers are using fake job offers to steal cryptocurrency
They have been hard at work on this operation
Just a tidbit, if a recruiter reaches out via Telegram, be weary
“Coding has become maybe 20% of his job”, understanding your requirements, and understanding what to review has become the job
Was interesting to read, a probable “prophetic” piece about the way we work
Qantas cuts executive bonuses by 15% after a July data breach
The 5.7M records impacted was first mentioned in a previous post
The Board decided to reduce annual bonuses in a show of shared accountability
Will this trend get some traction?
Breaches
Chess.com discloses recent data breach via file transfer app
Chess.com, hate it had to be them
Little detail is known about the breach as of now other than it was unauthorized access of a third-party FTP app
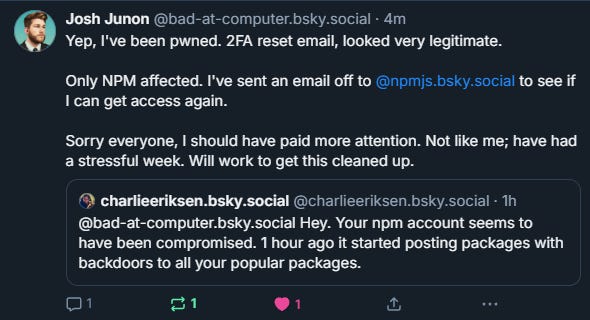
npm debug and chalk packages compromised
Having logs that account for package.json or the npm_packages table is what you would want to see if you’re impacted
The equivalent of npm list
The impact of this would be limited to crypto transactions on a hot wallet, but it serves as a threat model for open source project maintainers being targeted
The supply chain trend continues and is a hard problem to solve for
Update on Mandiant Drift and Salesloft Application Investigations
Some updates on the attack, the initial access is stll unknown, but the threat actor gained access to Drift’s GitHub organization and pivoted from there.
From the update: “we are advising all Drift customers to treat any and all Drift integrations and related data as potentially compromised”
Wrapping Up
In this post, we covered some of the top stories from this week.
Supply chain security, blast radius by proxy of vendors and how to approach these problems long-term still remain top of mind.
See you in the next one.