Possible SQL Injection Payload Detected
In this write-up, we’re going to be going over SOC165 — Possible SQL Injection Payload Detected from LetsDefend.
I was asked to go over this one by the folks over at LetsDefend, and I hope this helps those stuck or looking to get more hands on upskilling in. For more on this, check out this previous post.
FREE Stuff: Cybersecurity Resources To Add To Your Toolset
“If it’s free, take three". “If it’s free, it’s for me” - Unknown
Spoiler Alert: This write-up will have some answers to the LetsDefend Blue Team Training questions for this challenge. I’ll walk through the exercise without simply giving the answer to aid in your learning.
The Alert itself will give you the details to investigate.
When getting started, you’ll want to create a case
I found this to be a little non-intuitive in the platform, but you’ll need to do this in order to start the exercise.
Click Start Playbook
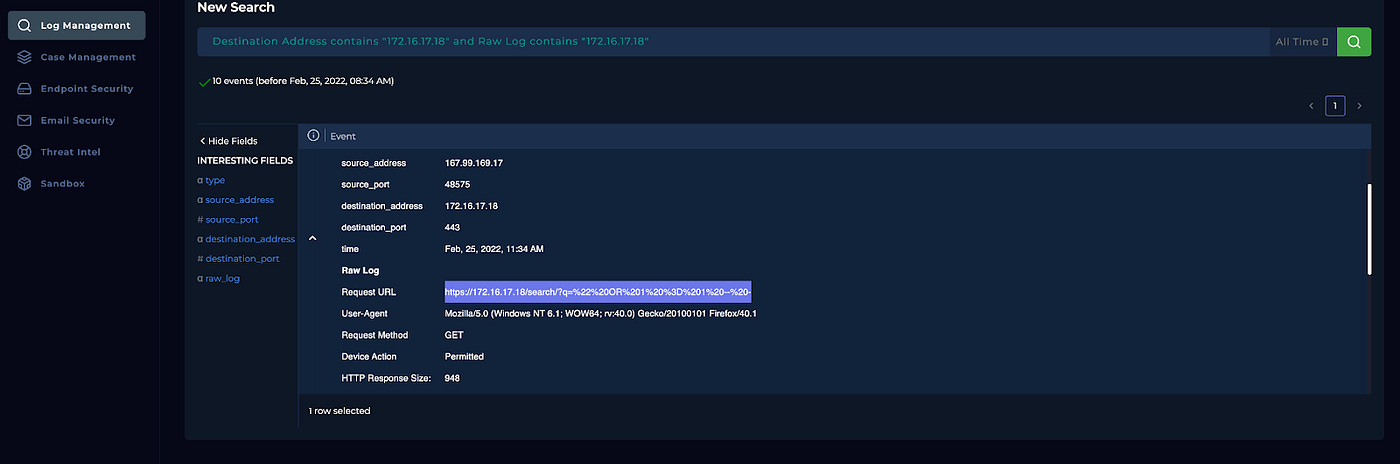
You see SQL activity when you decode the URL in the alert details.
https://172.16.17.18/search/?q=" OR 1 = 1 - -
User-Agent :
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1You can decode this with CyberChef or another similar tool. The key point here is the usage of OR 1 = 1 — -
This is a SQL statement used by attackers where a SQL injection vulnerability exists. Since 1=1 is always true, this will return what comes before OR 1=1 (i.e. dumping of the table) will be returned.
For more on this, see this section of the LetsDefend SQL Injection lesson detail
The decoded URL from the alert details also tells us the OS of the system via the User Agent information.
You can confirm this URL via the logs under “Log Management” when searching the raw logs.
This shows us what was being requested by the attacker.
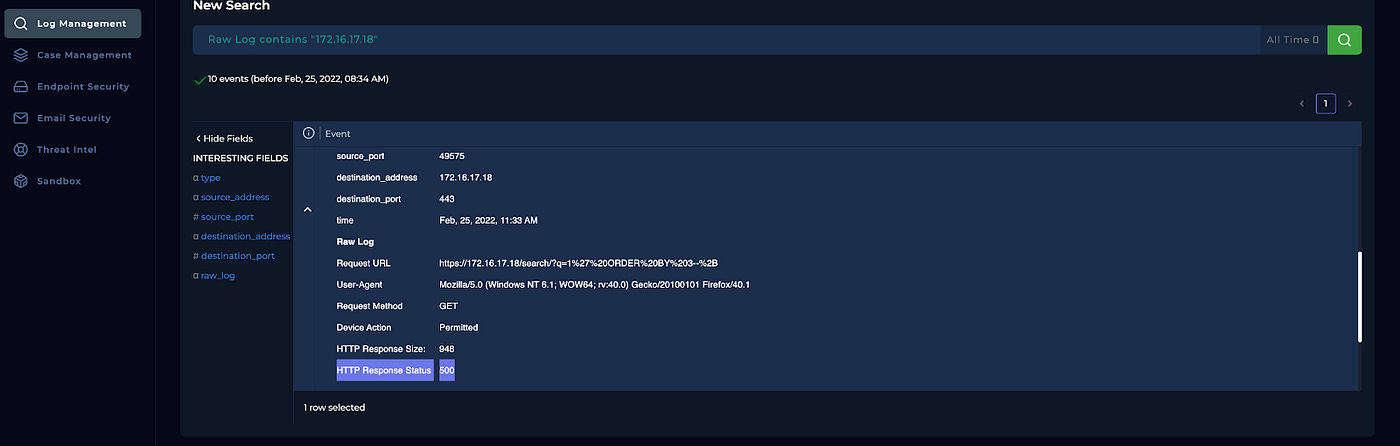
The HTTP Status codes are 500 Internal Server Error for all 5 SQL command injection attempts.
After these findings, we can say that this was an Unsuccessful attack as there were no commands in the logs to indicate success.
For more information on HTTP Status codes, see the following documentation
HTTP response status codes - HTTP | MDN
For the final question on this challenge, we are asked baout the direction of the traffic.
Since, this was Attacker → Target traffic, this would be Internet → Company Network.
For your Analyst Note, you can write something along the lines of
The decoded URL in the alert, indicates SQL injection.
After investigating the attempts from the attacker within the logs, the HTTP Status codes are 500 Internal Server Error. Meaning they were not successful.
Hope this helps!