In the ever-evolving landscape of Cybersecurity, the need for efficient tools to adapt is paramount. There are many tools that can facilitate.
Some call them SOAR, some call them XSOAR, at the end of the day whatever you decide to call it, what you want is the following.
Integrate different data sources in one place
Reduce the amount of clicks you have to make
Cut down on investigation time
Let’s review a platform that does just this.
Enter DTonomy, an automation platform specifically designed for Cybersecurity operations. Let’s cover it’s capabilities.
Understanding DTonomy's Core Capabilities
DTonomy serves as an advanced automation platform for Cybersecurity teams, offering a suite of playbooks, and workflows that address a wide range of challenges.
One of its primary objectives is to streamline and enhance the efficiency of routine tasks.
If you’ve worked in an Operations environment before, you know that sometimes you end up performing the same tasks or workflows over and over.
A lookup for an IP, or a domain. Running the same couple commands to check something in each alert and so forth. This is where automation comes into play.
Key Advantages of DTonomy
Operational Efficiency: Automates repetitive and time-consuming tasks, allowing Cybersecurity teams to focus on more strategic activities.
Enhanced Accuracy: Minimizes human errors through reliable processes.
You can do so leveraging the following: Nodes, Workflows, and Playbooks.
These three components are the building blocks of the platform.
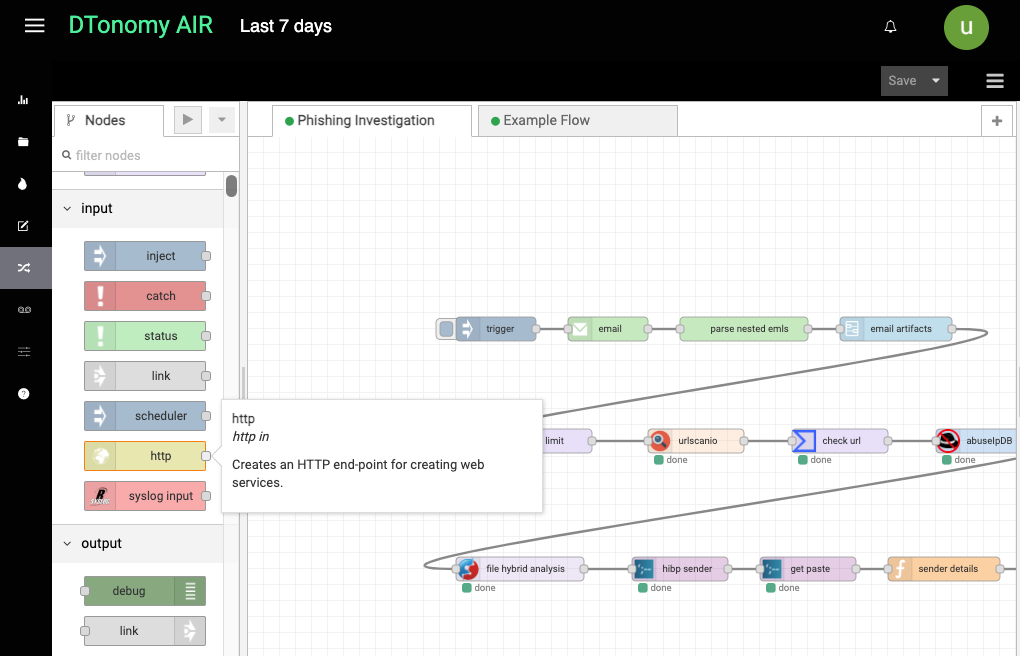
Above you can see the different nodes to choose from on the left panel. And on the right you see the nodes within the Playbook. In this Phishing Investigation playbook, you’ll see urlscanio, VirusTotal, AbuseIPDB, and Hybrid Analysis nodes to provide contextual data.
Nodes are where the integrations take place. They take input and generate output. For example, taking an http end point and outputting an http response.
To learn more on Nodes see the documentation here
Workflows are what actually runs the automations.
A playbook is then a template of a workflow.
In-Depth Analysis: Phishing Analysis Playbook
Let’s take a closer look at one of these Playbooks.
The Phishing Analysis playbook within DTonomy exemplifies the platform's robust capabilities in tackling specific Cybersecurity threats.
Phishing is still the #1 vector for attackers and it’s up to us to defend against this threat.
This playbook provides a comprehensive approach to identifying and mitigating phishing attacks.
Here’s a video overview of the Playbook.
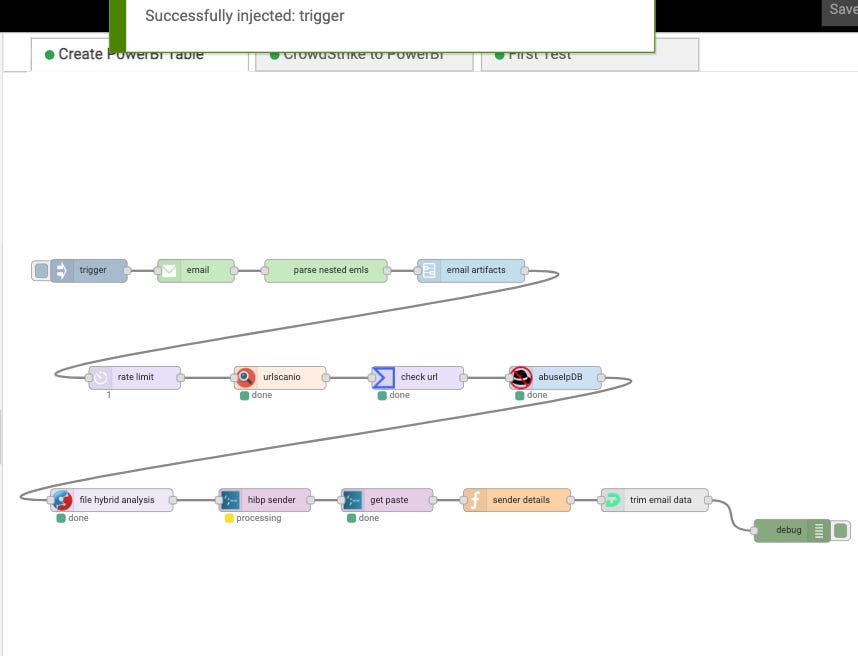
And big picture view of the Phishing Email Playbook
Components of the Phishing Analysis Playbook
Email Examination: The playbook initiates its process by analyzing suspicious emails. It examines email headers, URLs, and attachments to detect signs of phishing.
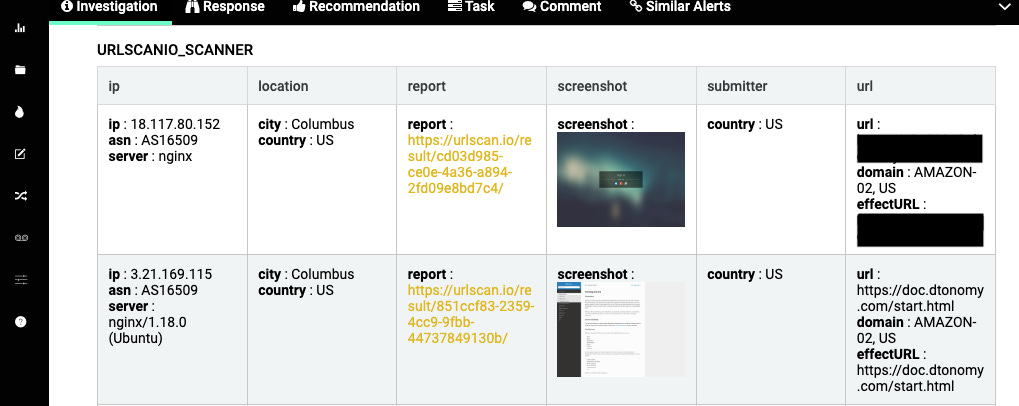
URL Analysis: Here it investigate’s URLs contained in the email, conducting reputation assessments to ascertain their legitimacy.
Attachment Scrutiny: The playbook performs an in-depth analysis to identify any malicious content. This includes malware signatures and sandboxing for observing the behavior of potentially harmful files.
Automated Response Mechanisms: Upon confirmation of a threat, a playbook can execute predefined response actions, such as isolating the suspicious email, or emailing relevant personnel.
What About Other Use Cases?
I went over the Phishing Email playbook which contains certain integrations (nodes) such as Hybrid Analysis, VirusTotal, urlscanio, since that is useful for this use case.
However, there are many options for you to automate parts of the Security Operations life.
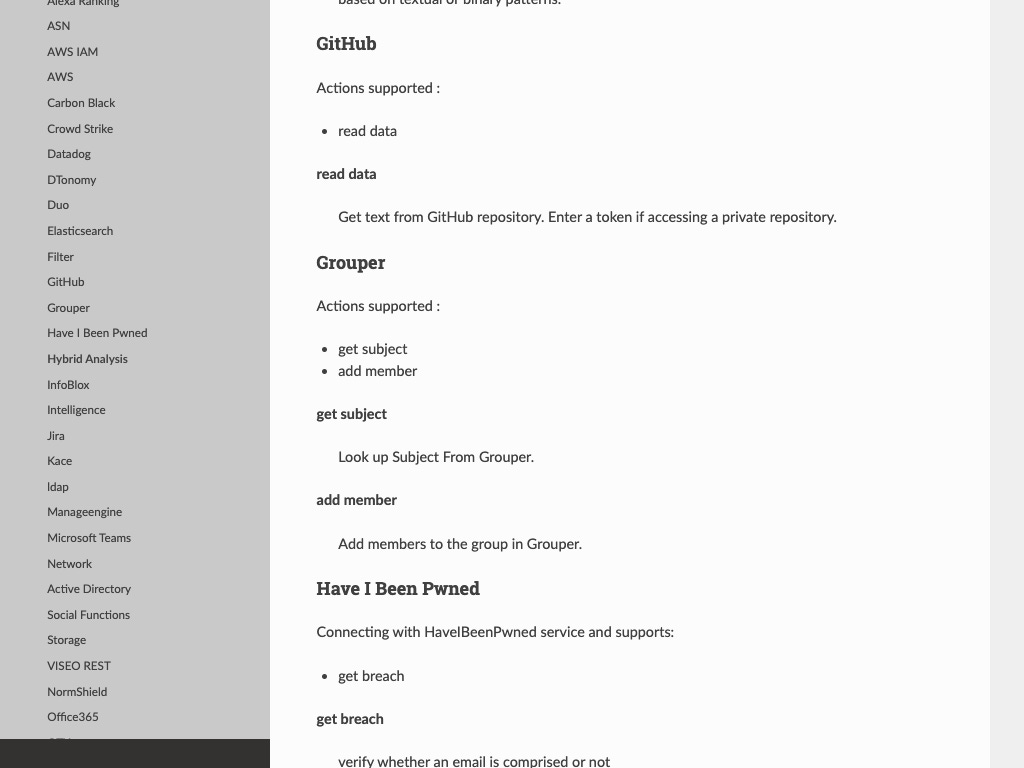
Here are some of the many integrations available in the platform.
You have Alexa Ranking, Github, Have I Been Pwned, and many more.
Alert Clustering
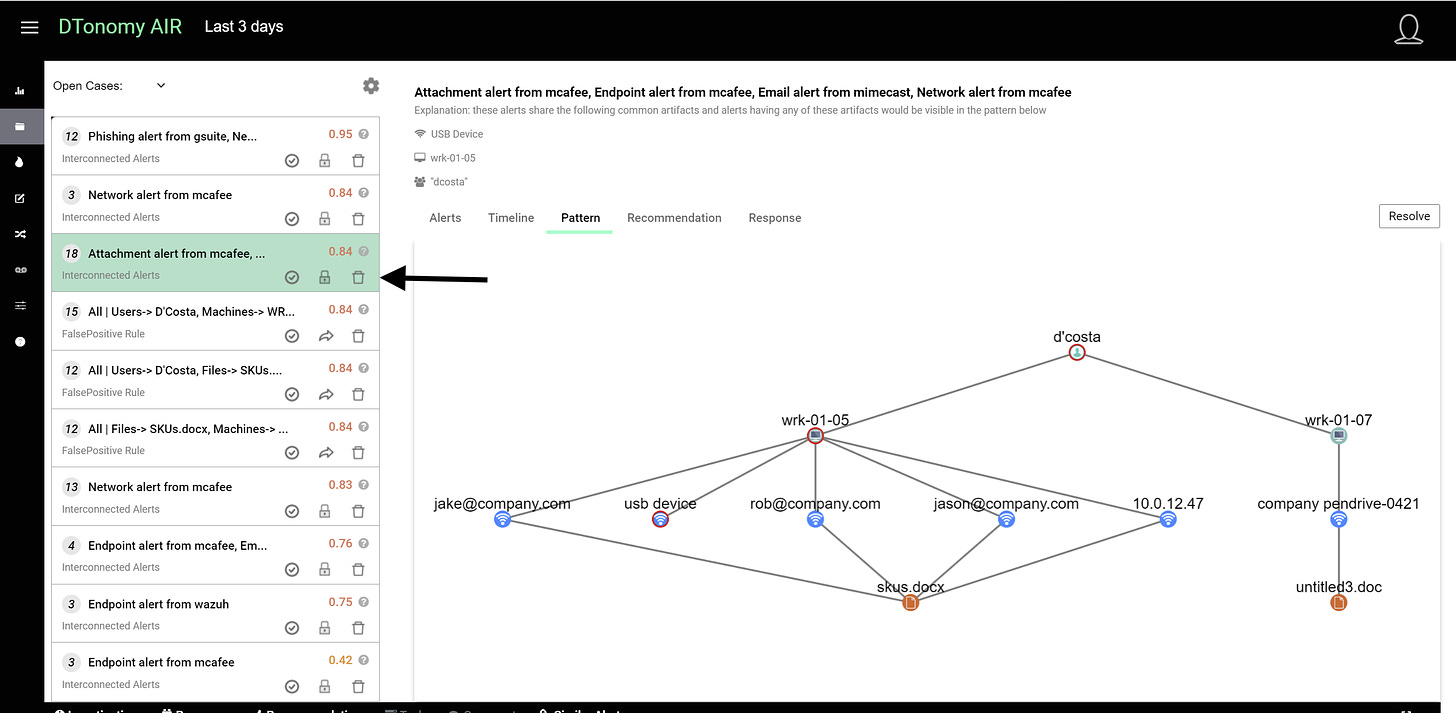
A problem that has been very hard to solve in the Security Operations and Detection and Response world is take many alerts based off of a common criteria, cluster them, and use that context to cross-correlate before you even have to investigate.
This would make it so you could have a hundred alerts, but in the end they are clustered into 15 final alerts or so, all with the context you need. By augmenting the manual cross-correlation process with AI-based discovery, security teams can analyze significantly more alerts in less time.
Here’s an example of what that would look like.
You have 10 groups that have the same artifacts, therefore these are grouped together. This is where you see “Interconnected Alerts”. You see the various data points such as user, email address, IP address, etc.
You can see how many alerts are clustered based off of the artifacts.
Concluding Thoughts
The DTonomy automation platform is something to take a closer look at.
We reviewed its Phishing Analysis playbook to see how automation is reshaping the Cybersecurity landscape. Along with the building blocks of the platform: Nodes, Workflows, and Playbooks.
It equips Security teams with the tools to be more effective, precise, and proactive in their response.
As we navigate the complexities of today’s threats, adoption of automation tools have become not just beneficial but essential for maintaining robust Cybersecurity defenses.
Disclaimer: This post is in partnership with DTonomy. All at no cost to you.