Previously, we’ve talked about Email Security and how you can do some analysis in with your email and be vigilant.
This series will go over the investigations around Email Security in depth, at the enterprise level.
Email investigations are an important part of Security investigations, this could include Phishing, Business Email Compromise (BEC), or Insider Threat related investigations.
This post focuses specifically on Google Workspace (Gmail for consumer end) aka
G Suite, though the principles discussed can apply broadly to all email providers. (Such as Microsoft Outlook or Office 365)
Google Workspace is an integral part of many companies, providing essential tools for the workplace. But from a Security standpoint, there’s also options for tools at our disposal.
We will go over some of the more useful features when it comes to these investigations.
Data Extraction in Google Workspace
There are three primary ways to extract data from Google Workspace: Admin Console, Google Vault, or the API.
Admin Console
Can export data for all users or specific accounts
Covers a wide range of data: Gmail, Drive, Calendar, Chat
Data is first archived in cloud storage, then it can be selectively downloaded
Security Investigation Tool will be the most common way you pull any of the above
Google Vault (For eDiscovery and Compliance)
Included in Business and Enterprise editions
A powerful tool for data retention, searching, and exporting. (Requires additional permission to utilize Vault)
The only method to access Gmail’s “Confidential Mode” messages
Supports retention policies, litigation holds, and compliance-related data archiving
Can search across Gmail, Drive, Shared Drives, Google Groups, Chat, Meet data
Provides search and filtering based on keywords, dates, and email addresses, etc.
Gmail API (For Custom Use Cases)
Allows programmatic access to Gmail data
Used by third-party email collection tools or for building custom forensic scripts
Useful for tracking actions like message deletion, marking emails as spam, or email forwarding
Audit Logging and Investigations
One of the most powerful aspects of Google Workspace is its audit logs, which help track user activity and identify security incidents. This can be logs such as User logs, Email Logs, OAuth logs, User reports.
Log Retention Periods:
Most logs are retained for six months, except for Email Log Search, which is available for only 30 days.
Organizations using Google Workspace Enterprise can store logs indefinitely in Google BigQuery or ship them to a SIEM for extended retention.
Email Header and Metadata Investigations
Google Workspace will have
Sender & recipient email addresses
Subject lines & timestamps
Return-Path, Content-Type
Message ID and client IP address
Mail delivery tracking (e.g., failures, spam filtering)
This provides you with what you’ll need for an investigation on a given suspicious email. As mentioned, I had a post going over this kind of header analysis here.
One thing to note, email headers do not contain email message content (only metadata). So to get the full contents of an email this would need to be done via one of the three above methods.
What I Read This Week
CEOs now learning self-defence to protect against cyber threats
I had to double take when I saw this too
The lines between digital and physical security are being blurred
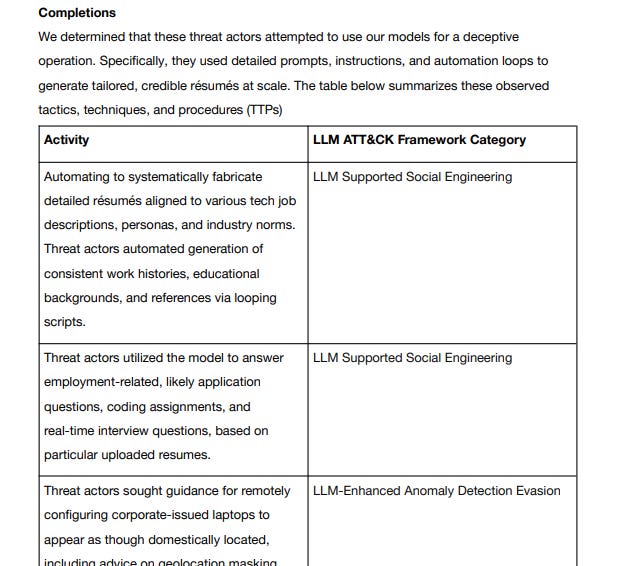
Disrupting malicious uses of AI: June 2025
I especially found interesting their Deceptive Employment Scheme: IT Workers case study
I previously talked about this in a few posts, including this one
Good insight into the DPRK operation that has been plaguing the industry, including TTPs
Security Isn’t A Solo Sport: Community, Burnout, and Identity at BSides312
Speakers at the conference went over the importance of human connections and communication
A refreshing reminder that at the end of the day we’re all human (for now)
Breaches
AT&T not sure if new customer data dump is déjà vu
* Cue the DJ Khaled gifs here *
Newer reports are saying this is repackaged data from their March 2024 breach
Ongoing cyberattack at US grocery distributor giant UNFI affecting customer orders
United Natural Foods discovered a breach on June 5 that has affected its distribution customers (namely Whole Foods)
Wrapping Up
Google Workspace provides robust tools and options for forensic investigations.
By leveraging the tools mentioned above, you can utilize them in your investigations.
Understanding these capabilities ensures that organizations can respond accordingly to email threats.
Stay tuned for the next part of this series.
See you in the next one.