Cybersecurity Interview Series
Security Operations Interviews
I’m bringing back the interview series.
If you’ve read my previous work on this, you’ll know that there’s not really a LeetCode or HackerRank equivalent for Cybersecurity interviews to prep with. Meaning, there’s not really a site that has resources earmarked for potential interviewing candidates.
Now, that is not to say Software Engineering interviews are easier or less daunting, simply pointing out the fact that the resources available are currently not at parity.
However, there is a collection of knowledge out there that we can use to help us be prepared for interviews in the field.
Below we will go over what could be asked on an interview for a Security Operations role (not meant to be exhaustive).
I will give a brief possible response for each and leave room for you to fill in the rest.
Note: This is meant to be a guide for Security Interviews but not a replacement for individual research and preparation.
Explain the difference in a vulnerability, risk and threat.
What you want to do here is define each and then give examples for each. Diving in on any follow up questions.
In a nutshell these 3 concepts and principles can be outlined as the following.
Vulnerability: Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat.
Risk: the level of adverse impact on operations, company assets, or individuals resulting from the impact of a threat and the likelihood of that threat occurring.
(src: NIST)
Threat: Any circumstance or event with the potential to adversely impact operations, assets, or individuals, through a system via unauthorized access, destruction, disclosure, modification of information.
This also can be summed up through the story of the 3 little pigs. More on that here.
Explain 2FA.
Two-factor authentication (2FA) is an extra layer of security used to ensure that people trying to gain access to an online account are who they say they are.
Being able to explain Multi-factor authentication, and which options are stronger than others is what you would need for a question like this.
First, a user will enter their username and a password. Then, they will be required to provide another piece of information. (something they know, something they have, or something they are).
You would then give examples of 2FA and why certain 2nd factors are stronger than others.
What is the CIA triad?
The three letters in "CIA triad" stand for Confidentiality, Integrity, and Availability.
For this concept, you would outline the definition of the CIA triad, explain each, and give a use case for each.
The CIA triad is a commonly used framework that forms the basis for the development of security systems.
Confidentiality: Confidentiality involves the efforts to ensure data is kept secret or private. A key component is ensuring that people without proper authorization are prevented from accessing important assets.
Use Case: encryption at rest.
Integrity: Integrity involves ensuring your data is trustworthy and free from tampering. The integrity of your data is maintained only if the data is authentic and accurate.
Use Case: hashing.
Availability: Systems, networks, and applications must function as they should and when they should. Individuals with access to information must be able to access it when they need to.
Use Case: S3 Backups, DNS.
What is AAA?
We’re not talking insurance here.
AAA within Cybersecurity stands for Authentication, Authorization, and Accounting.
You would outline the AAA framework, and give use cases for each.
Authentication: Authentication involves a user providing information about who they are. Users present login credentials that affirm they are who they claim.
Use Case: 2FA
Authorization: Authorization follows authentication. During authorization, a user can be granted privileges to access certain areas of a network or system.
Use Case: ACL’s
Accounting: Accounting keeps track of user activity while users are logged in to a network by tracking information such as their session length, their IP address, and the different services they accessed.
Use Case: SSO Logs
Analogy
This concept can be summed up with an analogy of getting into a venue or a club.
For example, say are looking to get into an exclusive venue. You dressed up nice, got spruced up, you get the idea.
You wait in line to get let in, and reach the front of the line. The security personnel asks for your named invitation, this serves as your ID. This is authentication. To prove you are who you say you are.
From here, the security personnel either lets you in or not. This is authorization. You are granted certain privileges such as entering the venue.
Finally, there are security cameras at the entrance door, and a few inside.
This is Accounting. Certain user activity is logged, such as timestamps of entering/exiting.
This framework and mental model of thinking within Cybersecurity: Authentication, Authorization, and Accounting is paramount to think big picture, and from there be able to zoom into the more minute problems.
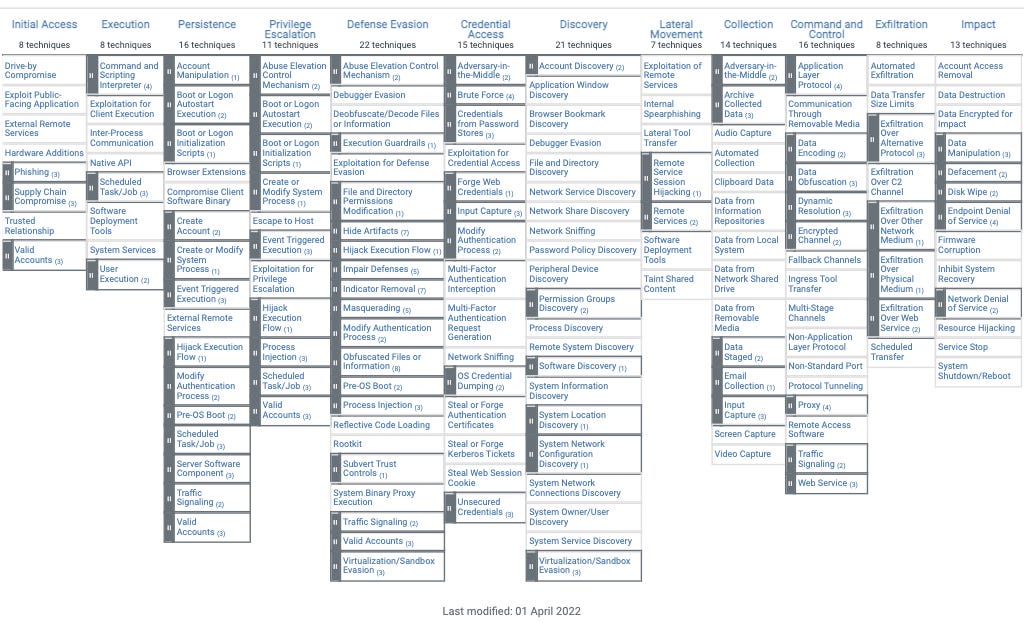
What is MITRE ATT&CK?
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. This knowledge base is used as a foundation for the development of threat models and methodologies in the private sector, government, and in the Cybersecurity product and service community.
For what it’s worth, it is the de facto standard used at tech companies.
(MITRE ATT&CK)
Now this is the MITRE ATT&CK color coded to show a heatmap for progress in alert coverage.
You can see the level of detail MITRE provides into an attack landscape.
Another cool thing about MITRE, is that they have matrixes for every OS, Mobile OS, most Cloud providers, and are constantly staying up to date with the technological advances of Cybersecurity.
You will want to be familiar with MITRE ATT&CK and how you would use it on the job.
What is a SIEM and it’s use cases?
Security information and event management (SIEM) is a security solution that provides the real time logging of events in an environment. The actual purpose for event logging is to detect security threats.
SIEM products generally have a number of features. The ones that interest SOC, DART and SecOps folks are: filtering the data that they collect and ability to create alerts for any suspicious events. (LetsDefend)
Even if you don’t have on the job experience working on a SIEM, having experience with open source platform ELK or Splunk free version will go a long way.
I also have an entire post on SIEMs. You can check it out here.
Do you have any projects that we can reference?
If you have any projects to show, ensure you prep discussing this before the interview.
This is where you can show your Github, blog you’re writing, or personal portfolio website. The main objective here is to have somewhere people can reference your work and your learnings, akin to “showing your work” back in Math class.
Having something here will definitely look good to potential employers as it shows you are putting in the work behind the scenes.
Wrapping Up
I know preparing for a interview, even more so a security interview can be a daunting task, but having a clear understanding of fundamental concepts such as the ones outlined above will help in landing that opportunity.
These are just some of the questions you can be asked in a Cybersecurity interview, geared towards Security Operations roles.
In a future post, we will go over scenarios in depth that can be covered in interviews, including technical interviews. These will be more geared towards mid-level roles. See you in the next one.