Cybersecurity Career Paths Recap
Here is a brief recap of the Career Path Series. In this series of posts, we went over a different domain of Cybersecurity each time. Different Blue Team career paths and what they look like.
We kicked off the series with Detection and Response, just because that’s where I’ve spent most of my time for a few years.
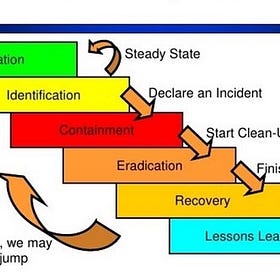
Cybersecurity Career Path: Detection and Response
In this series, we’re going to go over different career paths in Cybersecurity. In this issue, we’re gonna be doing a deep dive on Detection & Response and ...
Some of the job responsibilities could be
Ingesting logs
Normalizing those logs
Writing rules to alert on various threat activity
Responding to activity from those written rules
Log Analysis to tell a story of those events
There’s obviously more to the role, and there has been a lot of growth in this function, as shown in this report by Anvilogic x SANS.
Cybersecurity Career Path: Threat Hunting & Threat Intel
Previously we talked about Detection & Response and what the job entails and how Incident Response ties into it.
In a domain that has overlap with Detection & Response, Threat Hunting was covered in a following post. We went over the skill-set of a Threat Hunter and how Threat Intel intertwines with it.
Some of the core responsibilities could be
Threat research
Log Analysis
Baselining and Outlier analysis
One way to think about it Obtain Security Analytics -> Triage These > Hunt Lead > Contextualize the Lead
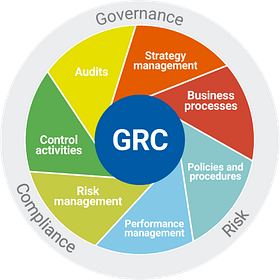
Cybersecurity Career Paths: GRC
One path within Cybersecurity that holds a lot of potential for growth is the one of Compliance and Governance, Risk, and Compliance (GRC).
GRC is a domain that can be either technical or non-technical making for a possible path for someone transitioning into the field of Cybersecurity.
Job responsibilities could look like the following
security assessments of third parties
security reviews for a a new tool
complying with frameworks such as SOC 2 and PCI DSS
We then covered career paths that involve the skillset of a Software Engineer.
Cybersecurity Career Path: Application Security
Continuing on with the Career Path Series, this will be a deep dive on Application Security, part 4 of the series where we discuss different career paths and roles within Cybersecurity.
A career in AppSec could look like
working on wide range of vulnerabilities reported via a bug bounty
static and dynamic code analysis
security design reviews
Incident response in Production
Cybersecurity Career Path: Infrastructure Security
In this post, we’ll be going over another domain of Cybersecurity: Infrastructure Security, otherwise known as InfraSec.
Another domain that is in the Software Eng family is Infrastructure Security. This is sort of like the Security Engineer for the Engineer.
A career in InfraSec could involve any of the following
implement secure by default control in CI/CD pipelines
building services to be utilized by other engineers
maintaining PKI and secrets management tools
What I Read This Week
How Phished Data Turns into Apple & Google Wallets
New tactics of carding, and the rise of the so-called “ghost tap”
Goes over the idea of value-based pricing (security tools) vs commodity pricing (software engineering tools)
The Underrated Cybersecurity Skill of Writing
The importance of writing on the job and writing beyond work
Conclusion
In the end, there are many paths you can go down in Cybersecurity. With 5 outlined in this recap, and in more depth in each respective post.
Thanks for reading. See you in the next one.
P.S. I worked on a Cybersecurity Interview Guide to help in the uphill battle that is interviews.
It’s a collection of interview questions and scenarios that you could face, that I’ve annotated over the years and put together in a Notion guide. This is available here