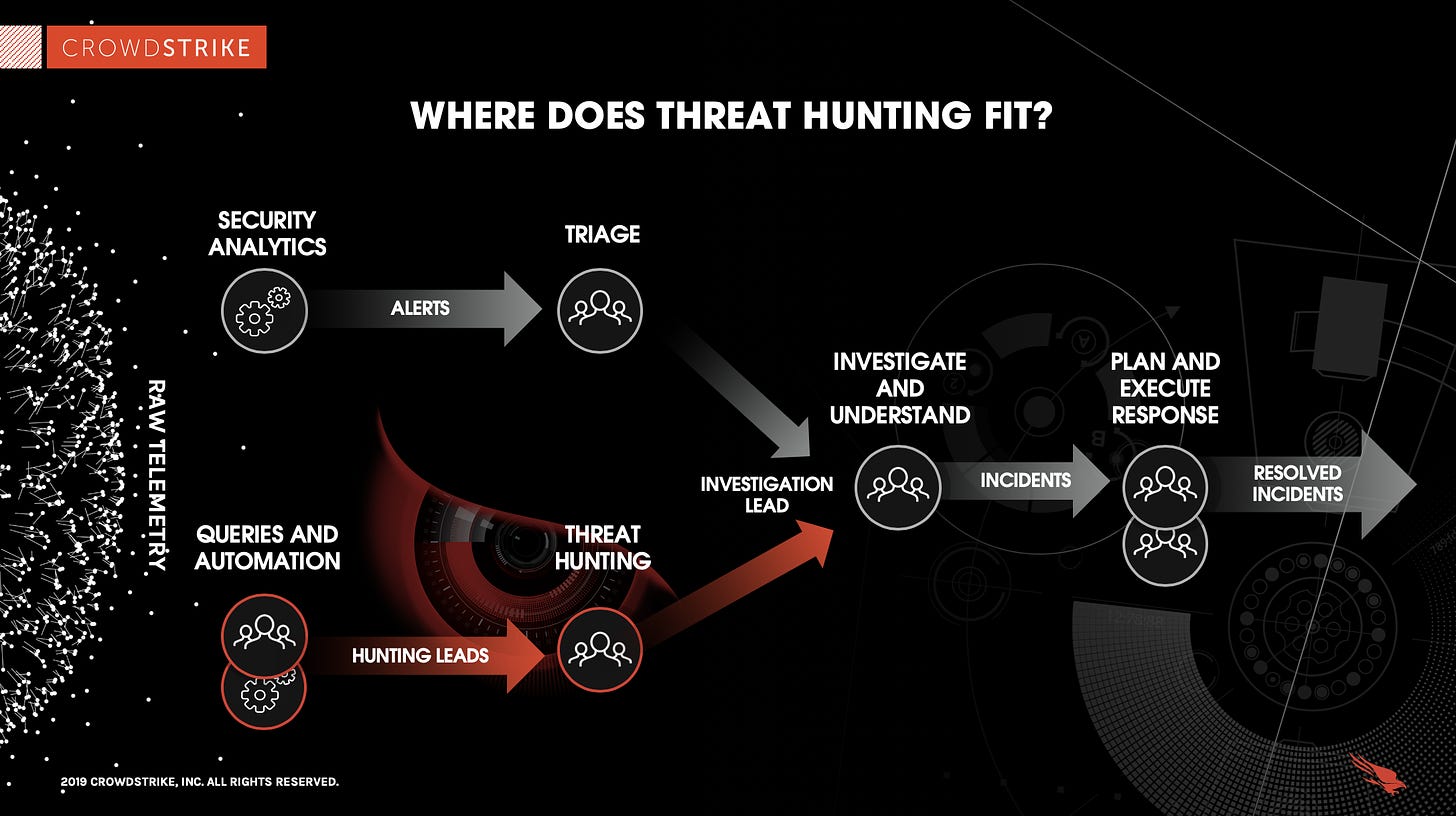
Previously we talked about Detection & Response and what the job entails and how Incident Response ties into it.
In this issue of the series, we’ll dive into another role within the Blue Team in Cybersecurity: Threat Hunting. These are generally closely aligned.
I wrote about how these two domains go hand in hand here.
Threat Hunting
In a nutshell, Threat Hunters proactively search for potential threats, focusing on areas not currently covered by any automated detection systems.
They use a variety of tools and techniques to identify suspicious activity, then work diligently to investigate and respond to these threats.
The above mentioned collaboration with Threat Intel will inform them on where best to focus their efforts. An informed defense is a strong defense.
A day in the life of a Threat Hunter could include tasks such as:
Threat Hunting Research & Planning
Data Analysis
Collaboration with the Blue Team
Documentation and Reporting findings
Let’s dive deeper into a sample job description.
Threat Hunting Research & Planning: reviewing the current threat landscape, noting any emerging trends or unusual activity. Use this information to develop hypotheses about potential threats, which will guide the day's threat hunting activities.
Data Analysis: After a hypothesis is formed, dive into the data. This involves analyzing logs, network traffic, endpoint data, etc. to identify anomalies or suspicious activity that could suggest a threat.
Investigation: When finding something that looks out of the ordinary, Threat Hunters will then start investigating. This could involve anything from time-lining logs, deep-dive network forensics to malware analysis.
Collaboration with the Blue Team: If the investigation uncovers a credible threat, collaboration with the rest of the Cybersecurity team will ensue to develop and implement a response strategy. This might involve patching vulnerabilities, taking systems offline, or image analysis.
Documentation and Reporting: At the end of the day, documenting your findings, making note of the threats identified, the steps taken to mitigate them, and recommendations for future action is key. This information is invaluable in preparing for future threats of similar nature.
These are the core responsibilities of the role, but not exhaustive.
Threat Intel
Now that we went over Threat Hunting and what the day to day could look like, let’s talk about Threat Intelligence.
Threat Intel professionals collect and analyze information about potential threats to the company. They then use this information to identify risks and develop strategies for responding to attacks, usually in collaboration with other Security teams.
In the end, the work will be tailored to their organization.
Many models exist to approach and illustrate threats such as the Diamond Model, or MITRE ATT&CK. These can be used to map adversaries, their capabilities and so forth.
A day in the life of a Threat Intel Analyst could include tasks such as:
Generating intelligence reports for stakeholders
Performing regular threat research to better understand the context of threats
Collaborative threat hunting efforts creating hypotheses about potential attacks.
Investigating threats to track their sources or attribution
This is not an exhaustive list, but a good overview on what to expect in the role.
The key part when it comes to Threat Hunting is collaboration.
Collaborating on Threat Hunting Efforts: Threat Intel Analysts play a key role in threat hunting activities (If a company is fortunate enough to have both a Threat Intel and Threat Hunting team). They create hypotheses based on the data collected and the intel gathered.
This involves answering questions such as
When did the events around the attack occur? (Forming a timeline)
What were the attacker’s objectives?
What systems were targeted?
What malware is/was used?
Think the Who, What Where, and so forth. The hypotheses help in understanding how the attacker thinks and where to look for more threat intelligence. This keeps everyone informed and aids in making risk assessed decisions.
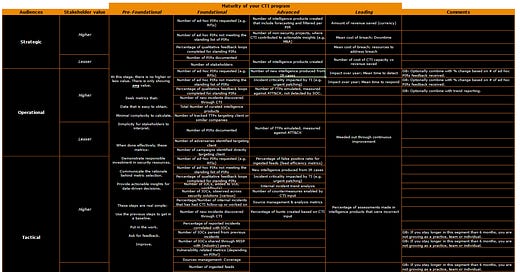
Once there is some level of maturity in the CTI program, there should be metrics to show progress and guide future efforts.
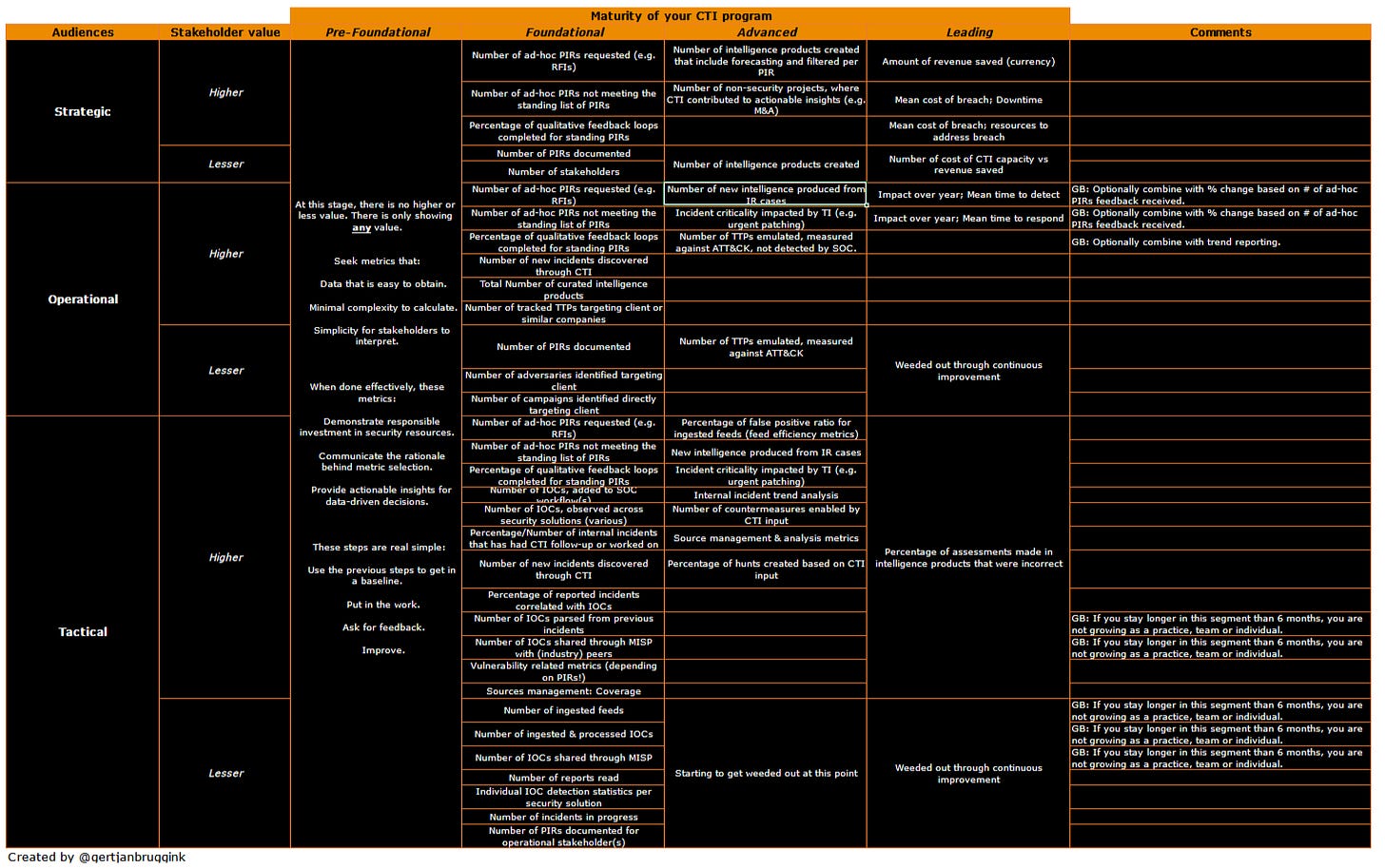
Every company’s risk exercises will look differently. This helps get the ball rolling.
See this subreddit for insight into the Threat Intel —> Threat Hunting dynamics.
What I Read This Week
AttackRuleMap: mapping of Atomic Red Team attack simulations to open-source detection rules
Cool repository outlining how detections could look like
Phishing Scam Imitates CrowdStrike Hiring Process
Recruitment Phishing campaign, leading to downloader for cryptominer
A Day in the Life of a Prolific Voice Phishing Crew
A full operation with roles and responsibilities better than some startups
Conclusion
As we went over in this post, Threat Intel and Threat Hunting go hand in hand and can give rewarding career paths. An opportunity to be on the front lines, proactively identifying and combating threats.
To dive deeper into this path, I highly recommend the book Huntpedia, a collection of value from people seasoned in the field. It’s free 😄.
Stay tuned for the next issue of this series, where we will look into another domain of Cybersecurity.